Pages
▼
Module to display the current working directory
The following module, on insertion into the kernel, displays the current working directory in the kernel space . The code is same as what is used in the system call getcwd.
The current working directory is saved as the member, name, of the structure qstr, which in turn is a member, d_name, of the structure dentry. Both the structures are found in dacache.h.
The pointer to the dentry is stored as a member, dentry, of the structure path which is defined in the file path.h
The file fs_struct.h defines a structure by the name fs_struct which has members,path and root, of type struct path.
The current pointer is of the type struct task_struct, this structure is defined in sched.h and the structure has a member fs of the type fs_struct.
Hence to access the value of the current working directory we need to trace the path
fs->path->dentry->d_name->name
*************************current_pwd.c**********************************
#include <linux/init.h>
#include <linux/module.h>
#include<linux/sched.h>
#include <linux/rcupdate.h>
#include <linux/fdtable.h>
#include <linux/fs.h>
#include <linux/fs_struct.h>
#include <linux/dcache.h>
MODULE_LICENSE("Dual BSD/GPL");
static int current_init(void)
{
char *cwd;
struct path pwd, root;
pwd = current->fs->pwd;
path_get(&pwd);
root= current->fs->root;
path_get(&root);
char *buf = (char *)kmalloc(GFP_KERNEL,100*sizeof(char));
cwd = d_path(&pwd,buf,100*sizeof(char));
printk(KERN_ALERT "Hello,the current working directory is \n %s",cwd);
return 0;
}
static void current_exit(void)
{
printk(KERN_ALERT "Goodbye cruel world");
}
module_init(current_init);
module_exit(current_exit);
***********************************************************************************
****************************Makefile*****************************
obj-m += current_pwd.o
all:
make -C /lib/modules/$(shell uname -r)/build M=$(PWD) modules
clean:
make -C /lib/modules/$(shell uname -r)/build M=$(PWD) clean
**************************************************************
Run the followig commands to compile and load.
$ sudo make
If there are no errors after compiling in the above step, we can insert the module using
$ sudo insmod current_pwd.ko
To see the output
$ dmesg
At the end of the messages you should see your current working directory being printed .
Send output from one terminal to another
If you are running a program in one terminal and want to view its output in another, here is a simple way to do it.
Open the the terminal in which you want to view the output
Run the command "tty"
The output should be some thing like "/dev/pts/<Number>" Note this down
Now open the terminal in which you want to execute the program and execute it, redirecting the output to the path that you got as the output to the "tty" command
for eg :
./test > /dev/pts/3
The output will appear in the other terminal instead of the one in which you are executing the program.
Open the the terminal in which you want to view the output
Run the command "tty"
The output should be some thing like "/dev/pts/<Number>" Note this down
Now open the terminal in which you want to execute the program and execute it, redirecting the output to the path that you got as the output to the "tty" command
for eg :
./test > /dev/pts/3
The output will appear in the other terminal instead of the one in which you are executing the program.
KVM introduction
KVM Introduction : 1
KVM which stands for kernel based virtualization is a linux kernel combined with the kvm kernel module tranforms the usual linux kernel into a bare metal hypervisor. Once KVM is installed into the kernel we can create Virtual machines in it and control them using various user space tools like qemu,libvirt or virsh.
Virtualizations Involves
CPU Virtualization
Memory Virtualization
I/O Virtualization
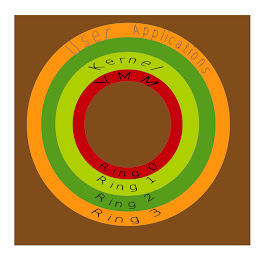
CPU Virtualization : To virtualize the CPU, KVM makes use of the hardware solution, that is CPUs which have virtualization instructions built into them . Intel calls this VT-X and AMD calls it AMD-V. The traditional architecture of CPUs had the standard ring based opertion as shown below.
The Operating system would execute the privileged instructions in the ring 0 and the user space applications would execute in the ring 3. The introduction of virtualization required that a new layer be present between the hardware and the operating system. This could have been achieved in two ways
0/1/3 model where the operating system is moved to the ring 1 and hypervisor is executed in the ring 0
0/3/3 model where the operating system and applications are both executed in the ring3 and the hypervisor executes in the ring 0.
Both these models move the operating system away from ring 0 leads to multiple problems because the operating system designed to always execute in ring 0. The software solutions like Binary translation and paravirtualization try to address the problems because of this change in the ring of operation of the operating system. The hardware solution introduced by Intel and AMD-V solve this by introducing new modes of operation in the CPU.
The intel Virtualization enabled hardare have new modes of operation VMX Root and VMX non root. The VMX root operation is used to execute the hypervisor and the VMX non root operation is used to execute the VM itself. Each of these modes of CPU have ring 0,1,2,3.
Thus the operating system can continue to operate in ring0 in VMX non root mode and thus retain all its control over the hardware just as a traditional opertaing systems. The hypervisor on the other hand executes in ring 0 in the VMX root mode. Thus even the hypervisor get the complete control of the hardware by being present in the ring0. But at any given time either othe VM or the hypervisor would be operating in the ring 0 mode. This takes care of a number of problems that exist in the software solutions of virtualization and also make the virtualization to be much quicker as the VM is able to operate on the hardware directly with out any intervention by the hypervisor during the normal operation. The control shifts out of the VM only on a I/O which is handled by the user space application running in the host kernel and interrupts or any other signals which are handled by the hypervisor.
KVM makes use of this hardware feature while running the virtual machines. Thus other than the traditional kernel space and user space there exits a new mode called as the guest mode of operation in the kernel. The VM opertes in this guest mode which makes use of the VMX non root mode. The guest OS works in the ring 0 of the VMX non root mode and the applications in the guest OS in the ring 3 of the VMX non root mode The KVM kernel on the other hand works in the ring 0 of the VMX root mode.
and the kernel which acts as the hypervisor executes in the kernel space of the vmx root mode.
CPU Virtualization
Memory Virtualization
I/O Virtualization
CPU Virtualization : To virtualize the CPU, KVM makes use of the hardware solution, that is CPUs which have virtualization instructions built into them . Intel calls this VT-X and AMD calls it AMD-V. The traditional architecture of CPUs had the standard ring based opertion as shown below.
0/3/3 model where the operating system and applications are both executed in the ring3 and the hypervisor executes in the ring 0.
Both these models move the operating system away from ring 0 leads to multiple problems because the operating system designed to always execute in ring 0. The software solutions like Binary translation and paravirtualization try to address the problems because of this change in the ring of operation of the operating system. The hardware solution introduced by Intel and AMD-V solve this by introducing new modes of operation in the CPU.
The intel Virtualization enabled hardare have new modes of operation VMX Root and VMX non root. The VMX root operation is used to execute the hypervisor and the VMX non root operation is used to execute the VM itself. Each of these modes of CPU have ring 0,1,2,3.
Thus the operating system can continue to operate in ring0 in VMX non root mode and thus retain all its control over the hardware just as a traditional opertaing systems. The hypervisor on the other hand executes in ring 0 in the VMX root mode. Thus even the hypervisor get the complete control of the hardware by being present in the ring0. But at any given time either othe VM or the hypervisor would be operating in the ring 0 mode. This takes care of a number of problems that exist in the software solutions of virtualization and also make the virtualization to be much quicker as the VM is able to operate on the hardware directly with out any intervention by the hypervisor during the normal operation. The control shifts out of the VM only on a I/O which is handled by the user space application running in the host kernel and interrupts or any other signals which are handled by the hypervisor.
KVM makes use of this hardware feature while running the virtual machines. Thus other than the traditional kernel space and user space there exits a new mode called as the guest mode of operation in the kernel. The VM opertes in this guest mode which makes use of the VMX non root mode. The guest OS works in the ring 0 of the VMX non root mode and the applications in the guest OS in the ring 3 of the VMX non root mode The KVM kernel on the other hand works in the ring 0 of the VMX root mode.
and the kernel which acts as the hypervisor executes in the kernel space of the vmx root mode.