Search
Audio/Sound output coming from both speaker and headphones at same time
On installation of a new version of linux it might happen that the audio/sound output keeps coming from the speaker of the laptop even after plugging in a headphone into its socket. The expected behaviour is that when we plug in the headphone, sound should only be coming in the headphone and nothing should be audible from the laptop speakers.
After going over number of possible solutions using available on the net what worked was updating the alsa driver by downloading the latest one from http://www.alsa-project.org/main/index.php/Download
The default version of driver installed was 1.0.23, but the update one available on the site was 1.0.25.
To solve the above mentioned problem download the latest driver source, compile it and install it using the following commands.
Assume that we have downloaded the driver for version 1.0.25 which has the package name alsa-driver-1.0.25.tar.bz2
Please note that the last step will require root permissions.
Now restart the system and the laptop speaker should get muted automatically on plugging in the headphones.
After going over number of possible solutions using available on the net what worked was updating the alsa driver by downloading the latest one from http://www.alsa-project.org/main/index.php/Download
The default version of driver installed was 1.0.23, but the update one available on the site was 1.0.25.
To solve the above mentioned problem download the latest driver source, compile it and install it using the following commands.
Assume that we have downloaded the driver for version 1.0.25 which has the package name alsa-driver-1.0.25.tar.bz2
Please note that the last step will require root permissions.
Now restart the system and the laptop speaker should get muted automatically on plugging in the headphones.
Creating directory under /proc in kernel 3.10 and above
In the post Creating a read write proc entry in kernel versions above 3.10 we saw the creation of read write proc entry. In the post we will see how to create folder under /proc and then create a entry under it.
To create a directory under /proc we can make use of the function
Where
name: is the name of the directory to be created. parent: parent is the name of directory under which the new directory has to be created.
To create a directory named "newparent" under /proc we will first declare a string having the name of the new folder
The NULL is passed for parent as we are creating the folder under /proc.
Once the new folder has been created we need to pass the pointer to struct proc_dir_entry to proc_create. The use of proc_create can be seen in the post
The full code for the module along with proc creation will be as shown below. Please refer to the post Creating a read write proc entry in kernel versions above 3.10 for more details
proc_dir.c
The makefile for the same
Compile and load the module using
If there are no errors then we can find the new proc entry under /proc
Thus we can see that under /proc a new folder called newparent has been created in which the proc entry hello has been created. We can read write to this proc entry like other proc entries
Related posts
Creating a read write proc entry in kernel versions above 3.10
Creating read only proc entry in kernel versions above 3.10.
Creating a proc entry - 1
To create a directory under /proc we can make use of the function
Where
name: is the name of the directory to be created. parent: parent is the name of directory under which the new directory has to be created.
To create a directory named "newparent" under /proc we will first declare a string having the name of the new folder
The NULL is passed for parent as we are creating the folder under /proc.
Once the new folder has been created we need to pass the pointer to struct proc_dir_entry to proc_create. The use of proc_create can be seen in the post
The full code for the module along with proc creation will be as shown below. Please refer to the post Creating a read write proc entry in kernel versions above 3.10 for more details
proc_dir.c
The makefile for the same
Compile and load the module using
If there are no errors then we can find the new proc entry under /proc
Thus we can see that under /proc a new folder called newparent has been created in which the proc entry hello has been created. We can read write to this proc entry like other proc entries
Related posts
Creating a read write proc entry in kernel versions above 3.10
Creating read only proc entry in kernel versions above 3.10.
Creating a proc entry - 1
Quiz Solution
Answers to Quiz based on chapter-4 of book linux device drivers 3rd ed
1. Which of the following config options need to be enabled to be able to debug kernel.
Ans.CONFIG_DEBUG_KERNEL
2.The first argument passed to printk specifies the
Ans.loglevel for the message to be printed
3.The command that can be used to view the kernel logs from user space is
Ans. dmesg
4. The function create_proc_read_entry returns a pointer to
Ans.struct proc_dir_entry
5.The seq file interface is used for
Ans. Passing kernel information to user space
6. Output of strace shows
Ans. The system calls made by a user application
7. In a kernel oops message EIP points to
Ans. The address of the faulty instruction
8. While using gdb for kernel debugging the kernel core file used passed to gdb is
Ans. /proc/kcore
9.Which of the following keys will launch the kdb
Ans. Pause
10. To use kgdb we need two systems connected by a serial cable
Ans. True
1. Which of the following config options need to be enabled to be able to debug kernel.
Ans.CONFIG_DEBUG_KERNEL
2.The first argument passed to printk specifies the
Ans.loglevel for the message to be printed
3.The command that can be used to view the kernel logs from user space is
Ans. dmesg
4. The function create_proc_read_entry returns a pointer to
Ans.struct proc_dir_entry
5.The seq file interface is used for
Ans. Passing kernel information to user space
6. Output of strace shows
Ans. The system calls made by a user application
7. In a kernel oops message EIP points to
Ans. The address of the faulty instruction
8. While using gdb for kernel debugging the kernel core file used passed to gdb is
Ans. /proc/kcore
9.Which of the following keys will launch the kdb
Ans. Pause
10. To use kgdb we need two systems connected by a serial cable
Ans. True
Enabling the traditional Alt+tab function in gnome3
In gnome3 the default bechiaviour of Alt + Tab is different from the traditional gnome behaviour. In gnome3 on pressing alt tab, it displays all the applications that are open, but if more than one window of the same application is open then all the windows are clubbed together and only the application is displayed.

To choose between the windows of the same application we need to wait on the required application or click on it and all the windows of that application gets displayed, and we can click on the window we want to open.
On the other hand the traditional alt tab swithches from one application to next in the order in which they were last used.
If we are not comfortable with this behaviour than we can make gnome perform like the traditions Alt+ tab as shown below.
Click on the activites tab and select the application Advanced Settings by typing "Advanced Settings" which will open a window as shown below.

On the left of the panel of the Advanced settings selec the option "Shell Extension" which will open the window as shown below.

Among the options on the right Turn on the option "Alternate Tab Extension"

Now close the advanced settings and the Alt+tab should start working the traditional fashion now.

To choose between the windows of the same application we need to wait on the required application or click on it and all the windows of that application gets displayed, and we can click on the window we want to open.
On the other hand the traditional alt tab swithches from one application to next in the order in which they were last used.
If we are not comfortable with this behaviour than we can make gnome perform like the traditions Alt+ tab as shown below.
Click on the activites tab and select the application Advanced Settings by typing "Advanced Settings" which will open a window as shown below.
On the left of the panel of the Advanced settings selec the option "Shell Extension" which will open the window as shown below.
Among the options on the right Turn on the option "Alternate Tab Extension"
Now close the advanced settings and the Alt+tab should start working the traditional fashion now.
Enabling autocompletion in gedit
While typing documents using gedit we can enable a very useful plugin called the autocompletion. This plugin will automatically prompt the words that have been typed previously in the document and hence save the time of retyping it.
To enable autocompletion in gedit click on
Edit->Prefernces
Click on the tab "plugins"

Move to the option word completion.

Enable it by checking the box on the left and close it.
Now when ever a document is being typed, gedit will automatically pop up the words that have been typed as the first letter of a word is typed. as shown below.

Please note that the autocompletion will work only on documents that have been saved and the new words that are typed will be shown in the autocompletion options only when the document has been saved after entering the new words.
To enable autocompletion in gedit click on
Edit->Prefernces
Click on the tab "plugins"
Move to the option word completion.
Enable it by checking the box on the left and close it.
Now when ever a document is being typed, gedit will automatically pop up the words that have been typed as the first letter of a word is typed. as shown below.
Please note that the autocompletion will work only on documents that have been saved and the new words that are typed will be shown in the autocompletion options only when the document has been saved after entering the new words.
Enabling Aplications drop down menu in gnome3
In the new gnome deskptops the applications menu that used to come as a drop menu to choose the applications to launch is not available by default.
But we can enable the drop down menu of applications by going to
Activites on the left corner.
Clicking on Applications tab
Click on Advanced settings
The following window will appear.

Now click on Shell extentions
Turn on The last option in the shell extentions

Applications Menu extention
Once this is turned on we should have the gnome symbol next to the activites tab, clicking on which will bring out the familiar pull down menu.
Activites on the left corner.
Clicking on Applications tab
Click on Advanced settings
The following window will appear.
Now click on Shell extentions
Turn on The last option in the shell extentions
Applications Menu extention
Once this is turned on we should have the gnome symbol next to the activites tab, clicking on which will bring out the familiar pull down menu.
Enabling snippets for languages in gedit
Snippets in gedit are some thing that will allow you to make the typing of repeated texts easier when we are diong programmig. To enable snippets in gedit frst we need to turn on the plugins.

Choose the tab titled plugins. Now browse down the list of plugins listed and look for the plugin named snippets. Enable snippers by checking the box next to it and closet h plugins menu.

Now click on

It will open window as shown below.

In the left column we can see a number of languages. Let us take html as an example. Click on the + mark beside HTML. It will open a list of all the commands of HTML. Click on which ever command you want to create shortcut for. For example we use the command
a number of times in HTML. To create a shortcut for break click on br.

On the right we will able to see the actual command that is below this window there will be options
Tab Trigger: What ever word is entered in against this option will act as a shortcut for the command.For example for break let us say we use the character "b" as the tab trigger word. While typing a html document using gedit we will need to only enter b and then press "tab" and the command will automatically get completed.
Shortcut Key : This is the combination of keys that when pressed will insert the command into the document. For example for "br" if you use the combination "cntrl + shift + space" , it means that in any html document that we create using gedit if we enter the above mentioned combination of keys the
command will automatically get inserted.
We can also create our own customized shortcuts using the options using the "+" key below left. On clcking on the "+" a new snippet option get added under which ever language we have selected. Give the name for the snippet and on the right insert the text you want to create shortcut for and on the options below add the shortcut we need to create for the text.
Choose the tab titled plugins. Now browse down the list of plugins listed and look for the plugin named snippets. Enable snippers by checking the box next to it and closet h plugins menu.
Now click on
It will open window as shown below.
In the left column we can see a number of languages. Let us take html as an example. Click on the + mark beside HTML. It will open a list of all the commands of HTML. Click on which ever command you want to create shortcut for. For example we use the command
a number of times in HTML. To create a shortcut for break click on br.
On the right we will able to see the actual command that is below this window there will be options
Tab Trigger: What ever word is entered in against this option will act as a shortcut for the command.For example for break let us say we use the character "b" as the tab trigger word. While typing a html document using gedit we will need to only enter b and then press "tab" and the command will automatically get completed.
Shortcut Key : This is the combination of keys that when pressed will insert the command into the document. For example for "br" if you use the combination "cntrl + shift + space" , it means that in any html document that we create using gedit if we enter the above mentioned combination of keys the
command will automatically get inserted.
We can also create our own customized shortcuts using the options using the "+" key below left. On clcking on the "+" a new snippet option get added under which ever language we have selected. Give the name for the snippet and on the right insert the text you want to create shortcut for and on the options below add the shortcut we need to create for the text.
Enabling minimize and maximize buttons in gnome3 (Debian7)
In gnome3 by default only the close button is available at the right corner and the buttons for minimize and maximize that we are used to are missing. We can enable these buttons using the following steps
Click on the Activites tab on the top left corner. Then click on the Applications tab and choose Advanced Settings. A window as shown below will pop up.

Choose the option "shell" from the left column. Now look at the option labeled
A pull down menu lists the combinations in which the buttons can be displayed . To show all the buttons choose the option "All" and close the settings.

Now both minimize and maximize buttons should appear on the top right.
Click on the Activites tab on the top left corner. Then click on the Applications tab and choose Advanced Settings. A window as shown below will pop up.
Choose the option "shell" from the left column. Now look at the option labeled
A pull down menu lists the combinations in which the buttons can be displayed . To show all the buttons choose the option "All" and close the settings.
Now both minimize and maximize buttons should appear on the top right.
Enabling and disabling touchpad clicks in gnome3 (debian 7)
The mouse clicks on touchpad of the mouse on the laptops can be enabled or disabled in gnome3 as required as shown below.
Click on the Activies tab on the top left. In the serch box that appears on the top right, type "Mouse and touchpad"
The following window will pop up.
The second tab is the tab for touchpad. In the touchpad tab, the options are
Disable touchpad while typing : Which will make sure that while we are typing if we touch the mouser pad the pointer will not move randomly.
Enable mouse clicks with touchpad : If this option is checked, we can use the touchpad to click too.
Click on the Activies tab on the top left. In the serch box that appears on the top right, type "Mouse and touchpad"
The following window will pop up.
The second tab is the tab for touchpad. In the touchpad tab, the options are
Disable touchpad while typing : Which will make sure that while we are typing if we touch the mouser pad the pointer will not move randomly.
Enable mouse clicks with touchpad : If this option is checked, we can use the touchpad to click too.
Enabling Desktop in Gnome 3 (Debian 7)
In the default settings in the genome 3 that comes with debian 7 there are no icons on the desktop and nothing happens even when we right click on the desktop. All the applications and windows can be managed by going to the activites tab on the right extreme.
But we can enable the desktop icons and handle it just like the classic gnome desktop by using the followint settings.
Click on Activities->Advanced settings
The following window will appear

Now click on the first option in the left column i.e. Desktop.
A number of options appear on the right of which the first one is

Move the slider from Off to On for this option and close the setting window.
Now we should able to see the similar icons of computer, file system, etc on the desktop.
Click on Activities->Advanced settings
The following window will appear
Now click on the first option in the left column i.e. Desktop.
A number of options appear on the right of which the first one is
Move the slider from Off to On for this option and close the setting window.
Now we should able to see the similar icons of computer, file system, etc on the desktop.
Unknown symbol cfg80211_scan_done
The following errors might occur while working with wireless drivers for linux.
These errors are basically because the modules lib80211 and cfg80211 are not loaded into the kernel. Thus we need to load these modules
Now the above symbols should be recognized.
These errors are basically because the modules lib80211 and cfg80211 are not loaded into the kernel. Thus we need to load these modules
Now the above symbols should be recognized.
Installing broadcom bcm43142 Wireless driver for linux
Most of the Linux distros do not have drivers for wireless bcm43142 wireless adapter. If your system has amd64 architecture then the driver can be for debian based systems can be installed using the command
or can be downloaded from
Download the package wireless-bcm43142-dkms_6.20.55.19-1_amd64.deb
Open a terminal and go to the directory where the above package is placed and run the command
To build the deb package yourself, download the package wireless-bcm43142_6.20.55.19.orig.tar.bz2 and run the following commands
The package wireless-bcm43142-dkms_6.20.55.19-1_amd64.deb will be available in the folder where the .tar.bz2 file was placed which can be installed as the previous .deb package.
The files on the above link work only for amd architecture, but for i386 the driver fails to build. For i386 architecture and non debian based systems download the source files from choose the files depending on 32bit or 64 bit architecture and run the following commands
If the module is compiled successfully try inserting it into the kernel
If the module inserts without error then the wireless should start working. It might throw an error Unknown symbol
To get around the problem, we need to inert modules on which the wl module depends on which are cfg80211 lib80211. Thus insert these modules first
Now insert the module
The wireless should start working now.
To make sure that we need not do the above steps every time we boot the system we can automate it using the following steps.
Copy the wl.ko to the folder /lib/modules/$(uname -r)/kernel/net/wireless
Now to see if the wl.ko module has been recognized along with its dependencies look into the file
Thus we can see that the wl.ko has been listed along with its dependent modules.
Now remove the module wl.ko that was inserted before
Insert it again using
If the module gets inserted with out any errors than put the above command into the file /etc/rc.local to make sure that the module gets inserted every time system boots.
Put the command before exit 0
Save the file and close it. Now reboot the system and the wireless should automatically start working on reboot.
If you can not find the files in the above links, you can get them from
BCM_Driver
Useful links
https://wiki.debian.org/IntroDebianPackaging
http://ubuntuforums.org/showthread.php?t=2123154
or can be downloaded from
Download the package wireless-bcm43142-dkms_6.20.55.19-1_amd64.deb
Open a terminal and go to the directory where the above package is placed and run the command
To build the deb package yourself, download the package wireless-bcm43142_6.20.55.19.orig.tar.bz2 and run the following commands
The package wireless-bcm43142-dkms_6.20.55.19-1_amd64.deb will be available in the folder where the .tar.bz2 file was placed which can be installed as the previous .deb package.
The files on the above link work only for amd architecture, but for i386 the driver fails to build. For i386 architecture and non debian based systems download the source files from choose the files depending on 32bit or 64 bit architecture and run the following commands
If the module is compiled successfully try inserting it into the kernel
If the module inserts without error then the wireless should start working. It might throw an error Unknown symbol
To get around the problem, we need to inert modules on which the wl module depends on which are cfg80211 lib80211. Thus insert these modules first
Now insert the module
The wireless should start working now.
To make sure that we need not do the above steps every time we boot the system we can automate it using the following steps.
Copy the wl.ko to the folder /lib/modules/$(uname -r)/kernel/net/wireless
Now to see if the wl.ko module has been recognized along with its dependencies look into the file
Thus we can see that the wl.ko has been listed along with its dependent modules.
Now remove the module wl.ko that was inserted before
Insert it again using
If the module gets inserted with out any errors than put the above command into the file /etc/rc.local to make sure that the module gets inserted every time system boots.
Put the command before exit 0
Save the file and close it. Now reboot the system and the wireless should automatically start working on reboot.
If you can not find the files in the above links, you can get them from
BCM_Driver
Useful links
https://wiki.debian.org/IntroDebianPackaging
http://ubuntuforums.org/showthread.php?t=2123154
Creating a read write proc entry in kernel versions above 3.10
In the post Creating read only proc entry in kernel versions above 3.10 we saw how to create a read proc entry in the kernel version 3.10 and above. In continuation to the same let us see how we can create a proc entry into which we can write data.
We can create a proc entry using the function
Where:
name: The name of the proc entry
mode: The access mode for proc entry
parent: The name of the parent directory under /proc
proc_fops: The structure in which the file operations for the proc entry will be created.
For example to create a proc entry by the name "hello" under /proc the above function will be defined are
For example to create a proc entry by the name "hello_write" under /proc the above function will be defined are
Now we need to create file_operations structure proc_fops in which we can map the read and write functions for the proc entry.
Next we need to add the functions read_proc and write_proc which will give write data to the proc entry and then read data from the proc entry.
The write function will recieve data from the user space using the function copy_from_user into a char pointer "msg".
Thus the write function will look as below.
Once data is written to the proc entry we can read from the proc entry using a read function, i.e tranfer data to the user space using the function copy_to_user function.
The read function can be as below.
The creation of proc entry and the intialization of the msg pointer can be done in a function create_new_proc_entry.
The create_new_proc_entry will be called in the init function.
The proc entry that was created will be removed in the exit function using remove_proc_entry.
Thus the full code for creating a write proc entry looks as below.
proc_rw.c
The makefile for the compilation of the modules are
Compile and load the module using
To test the proc entry let us first write data into the entry
Now we can read the data back
We can see that the message that we wrote into the proc entry, the same data is being displayed when it is read. The data will remain as long as it is not overwritten by new data.
Related Posts:
Creating read only proc entry in kernel versions above 3.10.
For kernel version before 3.10
Creating a proc entry - 1
Creating a proc read entry
We can create a proc entry using the function
Where:
name: The name of the proc entry
mode: The access mode for proc entry
parent: The name of the parent directory under /proc
proc_fops: The structure in which the file operations for the proc entry will be created.
For example to create a proc entry by the name "hello" under /proc the above function will be defined are
For example to create a proc entry by the name "hello_write" under /proc the above function will be defined are
Now we need to create file_operations structure proc_fops in which we can map the read and write functions for the proc entry.
Next we need to add the functions read_proc and write_proc which will give write data to the proc entry and then read data from the proc entry.
The write function will recieve data from the user space using the function copy_from_user into a char pointer "msg".
Thus the write function will look as below.
Once data is written to the proc entry we can read from the proc entry using a read function, i.e tranfer data to the user space using the function copy_to_user function.
The read function can be as below.
The creation of proc entry and the intialization of the msg pointer can be done in a function create_new_proc_entry.
The create_new_proc_entry will be called in the init function.
The proc entry that was created will be removed in the exit function using remove_proc_entry.
Thus the full code for creating a write proc entry looks as below.
proc_rw.c
The makefile for the compilation of the modules are
Compile and load the module using
To test the proc entry let us first write data into the entry
Now we can read the data back
We can see that the message that we wrote into the proc entry, the same data is being displayed when it is read. The data will remain as long as it is not overwritten by new data.
Related Posts:
Creating read only proc entry in kernel versions above 3.10.
For kernel version before 3.10
Creating a proc entry - 1
Creating a proc read entry
error: no such partition, grub rescue
If we come across the error in grub
It indicates that the partition on which grub was installed is no longer accessible. Which could be because it has been formatted or disconnected etc. There are a few ways of getting out of this situation.
If there is another partition on which we have a working OS we can boot into that OS using the following steps
The command in ls lists the partitions that grub is able to access.In the above example there are 3 partitions 1,2 and 4. If we know which among these has the working OS installed in it we can use the following set of commands to boot into it. Assume that (hd0,2) has the working OS.
Once we have booted into the working OS, if the another OS happens to be linux we can reinstall grub so that on next reboot the grub does not hang. To reinstall we need to find the partition on which grub needs to be installed which can be done using the command
The above output indicates that the hard disk on which operating system is installed is /dev/sda thus we can install grub using the command
If we do not have a working OS in any other partition then we need reinstall the grub using a live cd or a dvd or a live usb. Insert the live cd/dvd and boot the system. Once the live cd boots open a terminal and run the command
From the output look at the last column and the try to find the parition on which the os is installed. For example in the above case it is /dev/sda3.
Now execute the commands
The error should no longer appear.
Useful Links
http://www.gnu.org/software/grub/manual/html_node/GRUB-only-offers-a-rescue-shell.html#GRUB-only-offers-a-rescue-shell
http://www.gnu.org/software/grub/manual/html_node/Installing-GRUB-using-grub_002dinstall.html
http://howtoubuntu.org/how-to-repair-restore-reinstall-grub-2-with-a-ubuntu-live-cd#.UmgPBuHWSBs
For windows users
http://www.sevenforums.com/tutorials/20864-mbr-restore-windows-7-master-boot-record.html
It indicates that the partition on which grub was installed is no longer accessible. Which could be because it has been formatted or disconnected etc. There are a few ways of getting out of this situation.
If there is another partition on which we have a working OS we can boot into that OS using the following steps
The command in ls lists the partitions that grub is able to access.In the above example there are 3 partitions 1,2 and 4. If we know which among these has the working OS installed in it we can use the following set of commands to boot into it. Assume that (hd0,2) has the working OS.
Once we have booted into the working OS, if the another OS happens to be linux we can reinstall grub so that on next reboot the grub does not hang. To reinstall we need to find the partition on which grub needs to be installed which can be done using the command
The above output indicates that the hard disk on which operating system is installed is /dev/sda thus we can install grub using the command
If we do not have a working OS in any other partition then we need reinstall the grub using a live cd or a dvd or a live usb. Insert the live cd/dvd and boot the system. Once the live cd boots open a terminal and run the command
From the output look at the last column and the try to find the parition on which the os is installed. For example in the above case it is /dev/sda3.
Now execute the commands
The error should no longer appear.
Useful Links
http://www.gnu.org/software/grub/manual/html_node/GRUB-only-offers-a-rescue-shell.html#GRUB-only-offers-a-rescue-shell
http://www.gnu.org/software/grub/manual/html_node/Installing-GRUB-using-grub_002dinstall.html
http://howtoubuntu.org/how-to-repair-restore-reinstall-grub-2-with-a-ubuntu-live-cd#.UmgPBuHWSBs
For windows users
http://www.sevenforums.com/tutorials/20864-mbr-restore-windows-7-master-boot-record.html
exception emask 0x0 sact 0x0 serr 0x0 action 0x0
The following error might occur while the system boots.
To get around this we will need a live cd or a bootable usb. We can create a bootable usb using unetbootin. After booting using the live cd or the bootable usb, open a terminal and run the command
This will list all the disks available in the system. Choose the on in which linux is installed, assume it to be /dev/sda1. Now run the command
Answer yes for any repair related uestions thrown during the system check.
Once the check is over, reboot the system and try booting back into the ususal system. The error should no longer appear .
To get around this we will need a live cd or a bootable usb. We can create a bootable usb using unetbootin. After booting using the live cd or the bootable usb, open a terminal and run the command
This will list all the disks available in the system. Choose the on in which linux is installed, assume it to be /dev/sda1. Now run the command
Answer yes for any repair related uestions thrown during the system check.
Once the check is over, reboot the system and try booting back into the ususal system. The error should no longer appear .
Creation of proc entry using proc_create_data in kernel version 3.10 and above.
In the post "Creating read only proc entry in kernel versions above 3.10. " we saw how to create a proc entry using the function proc_create.
Note: The following module is valid only of kernel version 3.10 and above.
Another function available in kernel version 3.10 and above for creation of proc entry is proc_create_data which is defined in proc_fs.hs as
Where
name: The name of the proc entry
mode: The access mode for proc entry
parent: The name of the parent directory under /proc
proc_fops: The structure in which the file operations for the proc entry will be created.
data: If any data needs to be passed to the proc entry.
For example to create a proc entry by the name "hello" under /proc the above functions will be defined are
Along with creation of the entry we are also passing a function to the proc entry in using the porinter "msg".
Now we need to create file_operations structure proc_fops in which we can map the read function for the proc entry.
Next we need to add the function read_proc which will give to the user space the data that we want to export from the kernel space.
To access the data in the proc_dir_structure we need to make use of the function PDE_DATA to which we pass the file pointer. The function in turn returs a pointer to the data that was passed during the creation of the proc entry.
The message that we want to display will be defined in the function create_new_proc_entry in which we will also call the fuction for creation of proc entry.
The init and clean up functions for the module are
The full code for creation of proc entry using proc_create_data is
proc_read_data.c
The makefile for the compilation of the modules are
Compile and load the module using
We can see the output by using the cat command
Related Posts:
Creating read only proc entry in kernel versions above 3.10.
For kernel version before 3.10
Creating a proc entry - 1
Creating a proc read entry
Note: The following module is valid only of kernel version 3.10 and above.
Another function available in kernel version 3.10 and above for creation of proc entry is proc_create_data which is defined in proc_fs.hs as
Where
name: The name of the proc entry
mode: The access mode for proc entry
parent: The name of the parent directory under /proc
proc_fops: The structure in which the file operations for the proc entry will be created.
data: If any data needs to be passed to the proc entry.
For example to create a proc entry by the name "hello" under /proc the above functions will be defined are
Along with creation of the entry we are also passing a function to the proc entry in using the porinter "msg".
Now we need to create file_operations structure proc_fops in which we can map the read function for the proc entry.
Next we need to add the function read_proc which will give to the user space the data that we want to export from the kernel space.
To access the data in the proc_dir_structure we need to make use of the function PDE_DATA to which we pass the file pointer. The function in turn returs a pointer to the data that was passed during the creation of the proc entry.
The message that we want to display will be defined in the function create_new_proc_entry in which we will also call the fuction for creation of proc entry.
The init and clean up functions for the module are
The full code for creation of proc entry using proc_create_data is
proc_read_data.c
The makefile for the compilation of the modules are
Compile and load the module using
We can see the output by using the cat command
Related Posts:
Creating read only proc entry in kernel versions above 3.10.
For kernel version before 3.10
Creating a proc entry - 1
Creating a proc read entry
Creating read only proc entry in kernel versions above 3.10.
The creation of proc entries has undergone a considerable change in kernel version 3.10 and above. In this post we will see one of the methods we can use in linux kernel version 3.10 and above let us see how we can create proc entries in version 3.10 and above.
The function is defined in proc_fs.h as
Where:
name: The name of the proc entry
mode: The access mode for proc entry
parent: The name of the parent directory under /proc
proc_fops: The structure in which the file operations for the proc entry will be created.
For example to create a proc entry by the name "hello" under /proc the above function will be defined are
Now we need to create file_operations structure proc_fops in which we can map the read function for the proc entry.
Next we need to add the function read_proc which will give to the user space the data that we want to export from the kernel space.
The message that we want to display will be defined in the function create_new_proc_entry in which we will also call the fuction for creation of proc entry.
The init and clean up functions for the module are
The full code of module for creation of proc entry using proc_create is
The makefile for the compilation of the module is
Compile and load the module using
We can see the output by using the cat command
We can see that the message that we passed in the read function of the module is being displayed when the proc entry is read.
Related Posts :
For kernel version before 3.10
Creating a proc entry - 1
Creating a proc read entry
The function is defined in proc_fs.h as
Where:
name: The name of the proc entry
mode: The access mode for proc entry
parent: The name of the parent directory under /proc
proc_fops: The structure in which the file operations for the proc entry will be created.
For example to create a proc entry by the name "hello" under /proc the above function will be defined are
Now we need to create file_operations structure proc_fops in which we can map the read function for the proc entry.
Next we need to add the function read_proc which will give to the user space the data that we want to export from the kernel space.
The message that we want to display will be defined in the function create_new_proc_entry in which we will also call the fuction for creation of proc entry.
The init and clean up functions for the module are
The full code of module for creation of proc entry using proc_create is
The makefile for the compilation of the module is
Compile and load the module using
We can see the output by using the cat command
We can see that the message that we passed in the read function of the module is being displayed when the proc entry is read.
Related Posts :
For kernel version before 3.10
Creating a proc entry - 1
Creating a proc read entry
Adding a designer frame to an image using gimp in linx
We can add a designer frame to any photo using gimp by using following steps.
Open gimp and open the photo for which we need to add a frame by clicking on
We will use the following example image to add a frame to.

Now click on
As shown below.

This will pop a window with options for the frame as shown below.

The various options are
Frame Width : The width of the frame to added
Frame Fill: We can choose the fill the frame with
Color of our choise or, the same color as the background, the same color as the foreground or we can select any of the patterns available in gimp.
Texture Frame: We can add a texture from the various options of texture available. Texture Bump Map and Bump interactively are advanced options which we can explore once we are comfortable with the basics.
Bevel Index: How much slope needs to be added to the frame
Inner Shadow width : Width of the shadow of the frame
Innter Shadow Opacity :Opacity of the inner shadow.
Use layers : To retain the layers gimp creates for adding the frame, if the box is not checked gimp merges all the layers and creates a single layered image.
Now click on ok and we can see gimp will uickly add the frame as selected by the various options. The following is the result of addition of a frame to the above image.

Open gimp and open the photo for which we need to add a frame by clicking on
We will use the following example image to add a frame to.
Now click on
As shown below.
This will pop a window with options for the frame as shown below.
The various options are
Frame Width : The width of the frame to added
Frame Fill: We can choose the fill the frame with
Color of our choise or, the same color as the background, the same color as the foreground or we can select any of the patterns available in gimp.
Texture Frame: We can add a texture from the various options of texture available. Texture Bump Map and Bump interactively are advanced options which we can explore once we are comfortable with the basics.
Bevel Index: How much slope needs to be added to the frame
Inner Shadow width : Width of the shadow of the frame
Innter Shadow Opacity :Opacity of the inner shadow.
Use layers : To retain the layers gimp creates for adding the frame, if the box is not checked gimp merges all the layers and creates a single layered image.
Now click on ok and we can see gimp will uickly add the frame as selected by the various options. The following is the result of addition of a frame to the above image.
To find if cpu is 32bit or 64 bit in linux
Here are two ways of finding out,using linux, whether a processor on a system is 32bit or 64 bit.
1. Using proc entry.
Run the command
The above output clearly indicates that the address size of the cpu is 32 bits and hence does not support 64 bit.
2. Using the command cpuid.
For this we will have to install the package cpuid
After the installation run the command
From the above output too we can conclude that the cpu is a 32bit architecture.
1. Using proc entry.
Run the command
The above output clearly indicates that the address size of the cpu is 32 bits and hence does not support 64 bit.
2. Using the command cpuid.
For this we will have to install the package cpuid
After the installation run the command
From the above output too we can conclude that the cpu is a 32bit architecture.
Binary clock on linux terminal
Here is how we can create a binary clock on the Linux terminal. We will need to install the package binclock which can be done in the debian based systems
Now launch a terminal and run the command

To understand the output add the option "-n"

The binary time is in the format HH:MM:SS. The first column represents the first number of HH the second column the second number of HH and so on.
binclock by default provides the output in color which can be turned of by adding the option --color=off

Now launch a terminal and run the command
To understand the output add the option "-n"
The binary time is in the format HH:MM:SS. The first column represents the first number of HH the second column the second number of HH and so on.
binclock by default provides the output in color which can be turned of by adding the option --color=off
Creating pencil sketch of an image in linux using pinta
Here is how we can create the pencil skethc of any image using the software pinta in linux.
If you do not have pinta installed, you can install it using the package manager. In debian based systems we can run
Now launch pinta, In debian it would be listed under Applications->graphics, might be different for other distros.
Now click on

Browse the image for which the pencil sketch is need to be made, and click on open. Let us take the image of our beloved tux for creation of a pencil sketch.

Now click on

The following menu will pop.

Pencil tip size: Higher this value more dark the image looks.
Color range: Higher the value more mix of white and balck will appear in the image.
As the change in these options are done, the changes in the image can be seen in the backgroud. Which ever values are satisfctory click ok for those and the pencil sketch image is ready. Here is the pencil sketch image of tux.

If you do not have pinta installed, you can install it using the package manager. In debian based systems we can run
Now launch pinta, In debian it would be listed under Applications->graphics, might be different for other distros.
Now click on
Browse the image for which the pencil sketch is need to be made, and click on open. Let us take the image of our beloved tux for creation of a pencil sketch.
Now click on
The following menu will pop.
Pencil tip size: Higher this value more dark the image looks.
Color range: Higher the value more mix of white and balck will appear in the image.
As the change in these options are done, the changes in the image can be seen in the backgroud. Which ever values are satisfctory click ok for those and the pencil sketch image is ready. Here is the pencil sketch image of tux.
Adding fog effect using gimp
Here is how we can add the fog effect to any image, using gimp.
Lunch gimp and click on
Browse to the photo that is to which the fog effect has to be added and click on open.
In the example we will use the following image to add the fog effect.

Now click on

This will launch a window as shown below.

The options available are
Name: Layer Name Color: The color of the fog Turbulence: How much fog should be added to the image Opacity: How opaque should the fog be.
Click on OK and wait for gimp to do the magic.
After applying the fog, the above image looks as below.

Lunch gimp and click on
Browse to the photo that is to which the fog effect has to be added and click on open.
In the example we will use the following image to add the fog effect.
Now click on
This will launch a window as shown below.
The options available are
Name: Layer Name Color: The color of the fog Turbulence: How much fog should be added to the image Opacity: How opaque should the fog be.
Click on OK and wait for gimp to do the magic.
After applying the fog, the above image looks as below.
Quiz based on chapter-4 of book linux device drivers 3rd ed
Quiz on chapter-4 of book linux device drivers 3rd ed
Script to download the latest linux kernel
Here is a script that will download the latest kernel source kernel.org. THe script works on the current html page of kernel.org and might break if anything is changed in the page of kernel.org.
latest_kernel:
save the script as latest_kernel.sh.
Run the script by giving it execute permission. Please note that the from which ever folder the script is executed the user running the script needs to have the permission to create and delete files and folders as the script places the downloaded source in the same folder and also creates a temporary file and deletes it.
Thus we can see from the ouput that the latest kernel 3.10.4 has been downloaded. In case the download gets interrupted then the script will retry the download 3 times before quitting with the message of "Download Failed".
latest_kernel:
save the script as latest_kernel.sh.
Run the script by giving it execute permission. Please note that the from which ever folder the script is executed the user running the script needs to have the permission to create and delete files and folders as the script places the downloaded source in the same folder and also creates a temporary file and deletes it.
Thus we can see from the ouput that the latest kernel 3.10.4 has been downloaded. In case the download gets interrupted then the script will retry the download 3 times before quitting with the message of "Download Failed".
Difference between semaphores and spinlocks
In the posts " " we were introduced to semaphores and spinlocks and how they can be used to protect the critical section. Though both are used for the same purpose, their working is completely different from each other. Here are the major differences between the two.
1) Spinlocks can only be used for mutual exclusion, that is it can allow only one process into the critical region at any given time.
In semaphores we can use it for either mutual exclusion or it can be used as counting semaphore to allow more than on process into the critical region.
2) In spinlocks a process waiting for lock will keep the processor busy by continuously polling for the lock.
In semaphores a process waiting for a semaphore will go into sleep to be woken up at a future time and then try for the lock again.
3) In spinlocks a process waiting for lock will instantly get access to critical region as the process will poll continuously fro the lock.
In semaphores the process waiting for a lock might not get into critical region as soon as the lock is free because the process would have gone to sleep and will enter the critical region only when it is waken up.
4) Spinlocks can have only two values LOCKED and UNLOCKED.
Semaphores if used as mutex will have value 1 or 0, but used as counting semaphore it can have different values.
5)Spinlocks are not very useful in uniprocessor systems as they will keep the processor busy while polling for the lock, thus disabling any other process from running.
Semaphores don't keep the processor busy while waiting for the lock thus, they can be conveniently used in a uniprocessor system
6) It is recommended to disable interrupts while holding a spinlock.
Semaphores can he locked with interrupts enabled.
1) Spinlocks can only be used for mutual exclusion, that is it can allow only one process into the critical region at any given time.
In semaphores we can use it for either mutual exclusion or it can be used as counting semaphore to allow more than on process into the critical region.
2) In spinlocks a process waiting for lock will keep the processor busy by continuously polling for the lock.
In semaphores a process waiting for a semaphore will go into sleep to be woken up at a future time and then try for the lock again.
3) In spinlocks a process waiting for lock will instantly get access to critical region as the process will poll continuously fro the lock.
In semaphores the process waiting for a lock might not get into critical region as soon as the lock is free because the process would have gone to sleep and will enter the critical region only when it is waken up.
4) Spinlocks can have only two values LOCKED and UNLOCKED.
Semaphores if used as mutex will have value 1 or 0, but used as counting semaphore it can have different values.
5)Spinlocks are not very useful in uniprocessor systems as they will keep the processor busy while polling for the lock, thus disabling any other process from running.
Semaphores don't keep the processor busy while waiting for the lock thus, they can be conveniently used in a uniprocessor system
6) It is recommended to disable interrupts while holding a spinlock.
Semaphores can he locked with interrupts enabled.
Exctrating pages from a pdf document using gimp
Here is how we can use gimp to extract pages from a pdf file. Let us say we have a file named "make.pdf" with around 200 pages in it. If we need to extract the pages 10,11 from it.
We can either use the command line tool "pdftk" as shown in the post " " or we can use gimp as shown below. The big difference between the two being pdftk will extract them as pdf files itself, but gimp will extract them as images.
Launch gimp and click on
Browse to the file to be opened and click on open
Once the file is open ,gimp should launch a window as shown below. The various options available are
range: We can specify the range of pages that we wish to extract. For example if we wish to extract pages from page numbered 20 to 30 we can specify as 20-30. If the pages that we wish to extract are not in a continuous range we specify different page numbers separated by commas for example 2,4,6.
Open page as : The selected pages can be opened in one gimp document as different layers by selecting open pages as layers or we can create a gimp document for every page by selecting open pages as images. When extracting pages from a pdf, opening them as images seems like a better options as we can save each page separately. If we open it as layers then the pages will overlap each other and only the top page will be visible.
Then we can specify the width and height of the extracted pages and what resolution we want the pages to be in.
After specifying the above options as required, click on import.
If we have selected open pages as images, gimp will launch one document of every page extracted from the file as shown below.
We can save each of the documents separately in the desired format by clicking on
Note that the extracted pages will be images and we will be unable to copy any text from the files.
We can either use the command line tool "pdftk" as shown in the post " " or we can use gimp as shown below. The big difference between the two being pdftk will extract them as pdf files itself, but gimp will extract them as images.
Launch gimp and click on
Browse to the file to be opened and click on open
Once the file is open ,gimp should launch a window as shown below. The various options available are
range: We can specify the range of pages that we wish to extract. For example if we wish to extract pages from page numbered 20 to 30 we can specify as 20-30. If the pages that we wish to extract are not in a continuous range we specify different page numbers separated by commas for example 2,4,6.
Open page as : The selected pages can be opened in one gimp document as different layers by selecting open pages as layers or we can create a gimp document for every page by selecting open pages as images. When extracting pages from a pdf, opening them as images seems like a better options as we can save each page separately. If we open it as layers then the pages will overlap each other and only the top page will be visible.
Then we can specify the width and height of the extracted pages and what resolution we want the pages to be in.
After specifying the above options as required, click on import.
If we have selected open pages as images, gimp will launch one document of every page extracted from the file as shown below.
We can save each of the documents separately in the desired format by clicking on
Note that the extracted pages will be images and we will be unable to copy any text from the files.
Answers to Quiz on chapter-3 of book Linux Device Drivers- 3rd Edition
Answers to the Quiz
1.In the output of "ls -l /dev" a character driver is identified by
Ans. Letter c in the second column
2. The argument macro MAJOR is of type
Ans. dev_t
3. Which of the following function is used for static allocation of major number to character driver
Ans. register_chrdev_region
4. The structure file_operations is a
Ans. Collection of function pointers
5.The structure "file" is defined in the header file
Ans. linux/fs.h
6.cdev_alloc returns a pointer to
Ans. struct cdev
7.If the file_operation implementation of read returns 0 it signifies
Ans. End of file
8. The arguments passed to "open" method in a device driver are
Ans. inode pointer and file pointer
9. inode structure is used by the kernel internally to represent
Ans. All files
10. We can find out the major number of a driver by looking at the file
Ans. /porc/devices
1.In the output of "ls -l /dev" a character driver is identified by
Ans. Letter c in the second column
2. The argument macro MAJOR is of type
Ans. dev_t
3. Which of the following function is used for static allocation of major number to character driver
Ans. register_chrdev_region
4. The structure file_operations is a
Ans. Collection of function pointers
5.The structure "file" is defined in the header file
Ans. linux/fs.h
6.cdev_alloc returns a pointer to
Ans. struct cdev
7.If the file_operation implementation of read returns 0 it signifies
Ans. End of file
8. The arguments passed to "open" method in a device driver are
Ans. inode pointer and file pointer
9. inode structure is used by the kernel internally to represent
Ans. All files
10. We can find out the major number of a driver by looking at the file
Ans. /porc/devices
Quiz on chapter-3 of book Linux Device Drivers- 3rd Edition
Introduction to semaphores using animation
Semaphores can be defined as a tool to protect the access to a common resource while it is being accessed by multiple tasks or processes at the same time.
If the semaphore is used to allow access to the shared resource by only one process, then the semaphore is termed as a mutex or binary semaphore.
If the semaphore is used to allow access to the shared resource by more than one process, then the semaphore is termed as counting semaphore and the number of processes allowed to access the shared resource will depend on the initialization of the semaphore.
The basic functionality of semaphore is based on two operations or functions "signal" and "wait". Any process which needs access to a shared resource protected by a semaphore needs to call the function "wait" on the semaphore. If the semaphore is free then the process will be allowed to lock the semaphore and proceed to access the shared resource. On the other hand if the semaphore is already locked by another process then the new process will have to wait until the semaphore gets unlocked.
The piece of code which accesses the shared resource is generally termed as the critical region.
Any process holding a semaphore,when it is releasing the shared resource also has to release the semaphore by calling the function "signal" on that semaphore, thus enabling other functions waiting for the same semaphore to lock it and enter the critical section.
The internal working of a mutex, or binary semaphore is very simple. Every mutex is initially set to a integer value 1, which signifies that the mutex is in unlocked state. When a process calls the function wait on the mutex, the value of the semaphore is decremented by 1,thus making it 0. When the next process calls wait on the same mutex, the decrement of 1 from 0 will make the value negative, which will indicate to the process that the semaphore is not free and thus it can not enter the critical section. The process will increment the value back to 0 and then go into a wait or sleep state.
When a process calls the function signal on a mutex the value of the semaphore is incremented by 1, i.e. the value gets incremented to 1 from 0 making the semaphore available to other processes.
The following animation depicts the working of a binary semaphore.
In case of a counting semaphore the initial value of semaphore is set to the number of processes that are to be allowed into the critical section at the same time. If three processes need to be allowed into critical section then the initial value of semaphore will be set to three and each call of wait will decrement the value of semaphore by 1. Thus after three calls of wait, the value is semaphore would have reached 0 and any more calls to wait will make the number negative indicating the resource is busy.
Thus using semaphores we can successfully protect a critical section and restrict simultaneous access to a shared resource.
If the semaphore is used to allow access to the shared resource by only one process, then the semaphore is termed as a mutex or binary semaphore.
If the semaphore is used to allow access to the shared resource by more than one process, then the semaphore is termed as counting semaphore and the number of processes allowed to access the shared resource will depend on the initialization of the semaphore.
The basic functionality of semaphore is based on two operations or functions "signal" and "wait". Any process which needs access to a shared resource protected by a semaphore needs to call the function "wait" on the semaphore. If the semaphore is free then the process will be allowed to lock the semaphore and proceed to access the shared resource. On the other hand if the semaphore is already locked by another process then the new process will have to wait until the semaphore gets unlocked.
The piece of code which accesses the shared resource is generally termed as the critical region.
Any process holding a semaphore,when it is releasing the shared resource also has to release the semaphore by calling the function "signal" on that semaphore, thus enabling other functions waiting for the same semaphore to lock it and enter the critical section.
The internal working of a mutex, or binary semaphore is very simple. Every mutex is initially set to a integer value 1, which signifies that the mutex is in unlocked state. When a process calls the function wait on the mutex, the value of the semaphore is decremented by 1,thus making it 0. When the next process calls wait on the same mutex, the decrement of 1 from 0 will make the value negative, which will indicate to the process that the semaphore is not free and thus it can not enter the critical section. The process will increment the value back to 0 and then go into a wait or sleep state.
When a process calls the function signal on a mutex the value of the semaphore is incremented by 1, i.e. the value gets incremented to 1 from 0 making the semaphore available to other processes.
The following animation depicts the working of a binary semaphore.
In case of a counting semaphore the initial value of semaphore is set to the number of processes that are to be allowed into the critical section at the same time. If three processes need to be allowed into critical section then the initial value of semaphore will be set to three and each call of wait will decrement the value of semaphore by 1. Thus after three calls of wait, the value is semaphore would have reached 0 and any more calls to wait will make the number negative indicating the resource is busy.
Thus using semaphores we can successfully protect a critical section and restrict simultaneous access to a shared resource.
Introduction to critical section with animation
In modern operating systems, with support for multithreading and multiprocessor almost becoming default, it is common to come across the scenario where more than one process would try to access a resource simultaneously. The resource could be just a memory area or a hardware resource. Allowing access to a resource by multiple processes at the same time might not be recommended and the modern operating systems provide various tools to prevent such simultaneous access.
The piece of code which tries to access the shared resource is termed as the critical section of the program.
The following animation explains the concept of critical section using a general example.
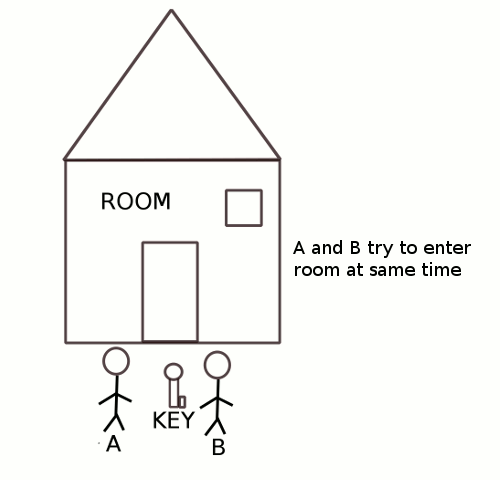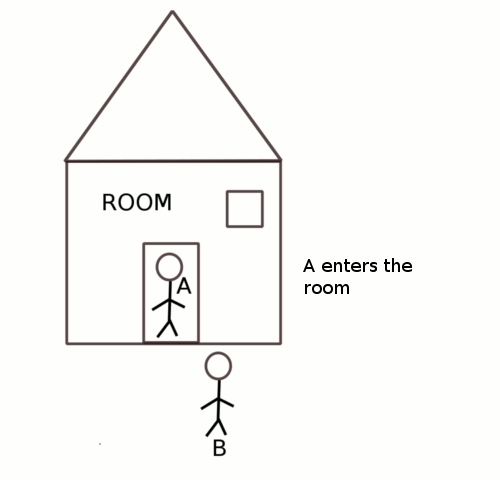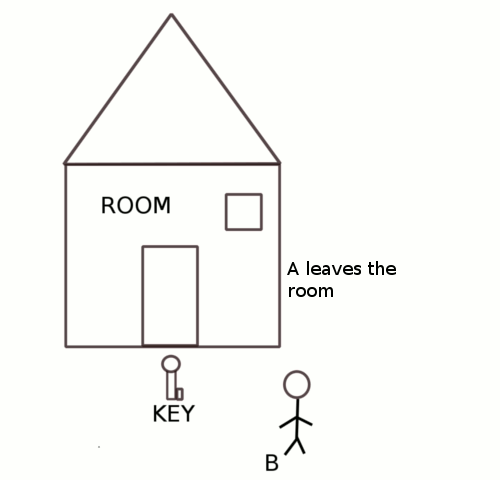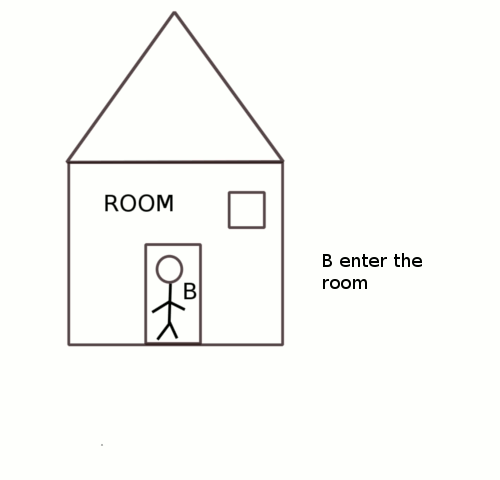
Two people A and B want to enter into a room at the same time. But only one person is allowed into the room at any given time.To ensure that only one person is allowed, the room is locked and only the person with the key to the lock is allowed into the room.
Let us a say both A and B reach the entrance but A gets the key before B then A will be allowed into the room and B will have to wait till A does not exit the room and frees the key. Only after A exits can B get hold of the key and enter the room.
With respect to operating systems, the persons A and B were equivalent to two processes, the room was the shared resource. The key was the tool used to ensure only one process gets access to the resource at any given time.
Two of the common tools available in operating systems to prevent multiple access to a shared resource are
The piece of code which tries to access the shared resource is termed as the critical section of the program.
The following animation explains the concept of critical section using a general example.
Two people A and B want to enter into a room at the same time. But only one person is allowed into the room at any given time.To ensure that only one person is allowed, the room is locked and only the person with the key to the lock is allowed into the room.
Let us a say both A and B reach the entrance but A gets the key before B then A will be allowed into the room and B will have to wait till A does not exit the room and frees the key. Only after A exits can B get hold of the key and enter the room.
With respect to operating systems, the persons A and B were equivalent to two processes, the room was the shared resource. The key was the tool used to ensure only one process gets access to the resource at any given time.
Two of the common tools available in operating systems to prevent multiple access to a shared resource are
- Spinlocks
- Semaphores
Adding antique border to imges using gimp
Using gimp we can make a photo look antique by adding the border to it like the older photos used to have.
Launch gimp, and open the photo to which the antique border is to be added using
Now click on
It will launch a menu as below
From the menu we can select
Click ok after entering the required values.
After gimp finishes its job, we should see the output as below.
The new image with the border can be saved in required format
Launch gimp, and open the photo to which the antique border is to be added using
Now click on
It will launch a menu as below
From the menu we can select
Click ok after entering the required values.
After gimp finishes its job, we should see the output as below.
The new image with the border can be saved in required format
Encrypting text files using VI editor
While creating text files using the "vi" editor we can make the files secure by encrypting the files with our own encryption key. Any encrypted file will be unreadable unless the coorect key is not known.
Let us say we have a file by the name temp:
To encrypt this file, so that no one with out the encryption keys is able to read or write from the file, open the file using vi editor
Now go to command mode by typing "esc"
Then type :X and press enter.
Note the "X" is in upper case
VI will now prompt for an encryption key as shown below.
Enter any key, and press enter
It will prompt for confirmation of the key, enter the same key again .
To find out whether the file is encrypted or not we can use the command file
Thus indicating that it is an encrypted file. If we try to read from the file using cat
The output will be junk value. If we try to open the file using "vi" editor, it will prompt us for the encryption key.
In case we entered the wrong key, the file will open but with garbage values in it, and it will be in read only mode.
Only on entering the correct key, the file be visible in the original form
To remove the encryption, open the file using "vi" editor by entering the correct key and go to the command mode. Use the command
And press enter. It will prompt for a value of key, hit enter, do not enter any value for the key.
The encryption should have been removed now and we can edit the file as usual way.
Let us say we have a file by the name temp:
To encrypt this file, so that no one with out the encryption keys is able to read or write from the file, open the file using vi editor
Now go to command mode by typing "esc"
Then type :X and press enter.
Note the "X" is in upper case
VI will now prompt for an encryption key as shown below.
Enter any key, and press enter
It will prompt for confirmation of the key, enter the same key again .
To find out whether the file is encrypted or not we can use the command file
Thus indicating that it is an encrypted file. If we try to read from the file using cat
The output will be junk value. If we try to open the file using "vi" editor, it will prompt us for the encryption key.
In case we entered the wrong key, the file will open but with garbage values in it, and it will be in read only mode.
Only on entering the correct key, the file be visible in the original form
To remove the encryption, open the file using "vi" editor by entering the correct key and go to the command mode. Use the command
And press enter. It will prompt for a value of key, hit enter, do not enter any value for the key.
The encryption should have been removed now and we can edit the file as usual way.
Subscribe to:
Posts (Atom)